APRIL 22, 2024 UPDATE: This campaign is now using "tickets-lastpass[.]com" as its primary phishing page and appears to have shifted primarily to texting (SMS messages) as the main point of contact, though the cybercriminals are also still calling people directly in an attempt to social engineer people towards visiting the new phishing site. Please report any communications claiming to be from LastPass using this URL and be aware this is a malicious site.
APRIL 19, 2024 UPDATE: As we noted may happen, this phishing campaign has begun a new phase and customers have reported seeing calls and texts. Please see below for steps you can take to protect yourself:
- Ignore any unsolicited or unprompted incoming phone calls (automated or with a live individual) or texts claiming to be from LastPass related to a recent attempt to change your password and/or account information. These are part of an ongoing phishing campaign.
- If you do see this activity and are concerned you may have been compromised, please contact us at abuse@lastpass.com
- As always, we will NEVER ask you for your password.
LastPass would like to raise awareness to a recent phishing campaign affecting our customers related to the CryptoChameleon phishing kit which has been associated with crypto thefts (more information on this kit can be found here). This campaign was initially brought to our attention by our friends at Lookout, and we’d like to thank them for being good partners and proactively sharing their findings. A phishing kit is a phishing-as-a-service software offering that allows threat actors to easily create fake SSO or other login sites drawn from fraudulent branding (including graphics and logos) to imitate a site or company for which the threat actor is seeking collect credentials. Basically, a cybercriminal can use these kits to create fake websites to steal passwords and other authentication data and either use these credentials themselves or sell them to other criminals. Victims are directed to fake websites via phishing emails, SMS messages, or even direct phone calls (vishing). We have worked with our vendor partners to take down the phishing site, and we are informing our customers so they can be on the lookout for future iterations of this campaign that may use the same tactics.
Overview
Initially, we learned of a new parked domain (help-lastpass[.]com) and immediately marked the website for monitoring should it go live and start serving a phishing site intended to imitate our login page or something similar. Once we identified that this site went active and was being used in a phishing campaign against our customers, we worked with our vendor to take down the site.
Tactics Associated with This Campaign
In general, these are the tactics we have observed associated with this campaign:
- The customer receives a call from an 888 number claiming their LastPass account has been accessed from a new device and instructing them to press “1” to allow the access or “2” to block it.
- If the recipient presses “2”, they are told they will receive a call shortly from a customer representative to “close the ticket.”
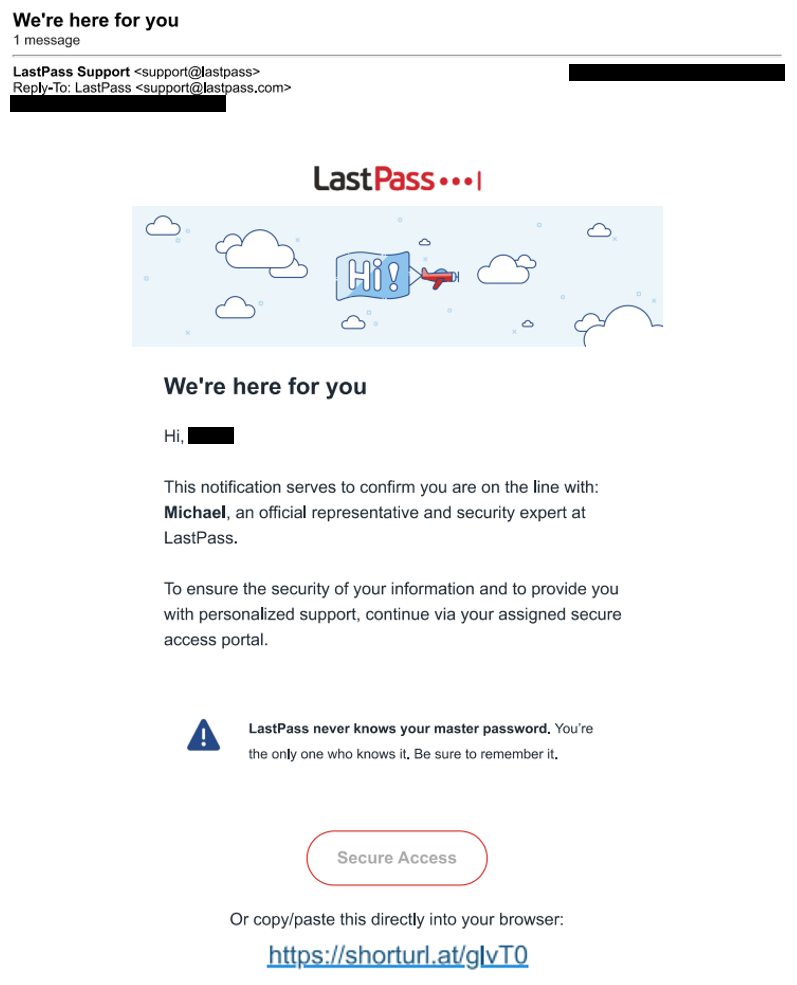
- The recipient then receives a second call from a spoofed phone number and the caller identifies themself as a LastPass employee. This individual typically has an American accent. The caller will send the recipient an email they claim will allow them to reset access to their account. This will actually be a phishing email with a shortened URL that will send them to the “help-lastpass[.]com” site designed to steal the user’s credentials.
- If the recipient inputs their master password into the phishing site, the threat actor attempts to log in to the LastPass account and change settings within the account to lock out the authentic user and take control of the account. These changes may include changing the primary phone number and email address as well as the master password itself.
What To Do
As we noted above, we have worked hard to disrupt this phishing campaign and have had the initial phishing site taken down. However, as the initial phishing kit itself continues to offer LastPass branding, we are sharing this information so that our customers can be aware of these tactics and take the appropriate response should they receive a suspicious call, text, or email.
- If you receive a suspicious phone call claiming to be from LastPass, simply hang up and please send us an email with the details of the call to abuse@lastpass.com.
- If you receive a suspicious text claiming to be from LastPass, please send a screen capture of the text to abuse@lastpass.com.
- If you receive an email you believe may be related to phishing, please forward the email as an attachment to abuse@lastpass.com.
Please remember that no one at LastPass will ever ask for your master password.
We will continue to work diligently to protect our customers and take whatever proactive measures we can to disrupt this activity. For more information about how to recognize phishing attempts and suspicious online activity, view Protect Yourself from Social Engineering Attacks. For tips and suggestions for protection against these types of attacks, view Recommendations for Protecting Yourself From Social Engineering Attacks.
Actual phishing site: “help-lastpass[.]com” and "tickets-lastpass[.]com"
Shortened URL Embedded in Email: shorturl[.]at/glvT0
Phishing Email Subject Line: We’re here for you
Spoofed Sender: Shows as LastPass Support <support@lastpass>
*Note there is no “.com” included in the displayed email address