Attackers are using the TeamFiltration pentesting framework to conduct brute-force attacks against Microsoft Entra ID accounts in an ongoing campaign, according to Proofpoint. TeamFiltration is designed to simulate account takeover (ATO) attacks in Microsoft cloud environments, specifically targeting Entra ID (formerly Azure Active Directory). Entra ID is a core component of Microsoft’s cloud identity and access management services and is widely used, especially among small and medium sized businesses. This campaign strategy combines trusted platforms, global infrastructure, and evasive techniques to maximize impact while minimizing detection. This campaign is an efficient way to breach cloud environments by essentially taking advantage of weak passwords. Passwords were the primary target and attack vector in this campaign which demonstrates that even in a cloud-first world, password hygiene is still a frontline defense.
Campaign details
TeamFiltration has historically been a popularly exploited legitimate tool since it was released in 2021 because the tool provides both white and black hat hackers with a solid framework to take over Office 365 Entra ID accounts, data exfiltration, and persistent access. Proofpoint attributed the recent surge in login attempts to UNK_SneakyStrike. Starting in December 2024 and peaking in January 2025, this campaign has targeted over 80,000 user accounts across approximately 100 cloud tenants or organizations and have resulted in multiple successful account takeovers. How passwords factored into the attack:
- Enumeration first: The attackers used the Microsoft Teams API to identify valid usernames within organizations and ensure they weren’t wasting time on nonexistent accounts.
- Password spraying: Once UNK_SneakyStrike had a list of valid usernames, they launched waves of login attempts using common passwords like “Password123.” These attempts were spread across Amazon Web Services (AWS) servers in different regions to avoid detection.
- Account takeover: If a password matched, the attacker gained access to the account. From there, they could exfiltrate data, move laterally, or maintain persistence using tools like OneDrive backdoors.
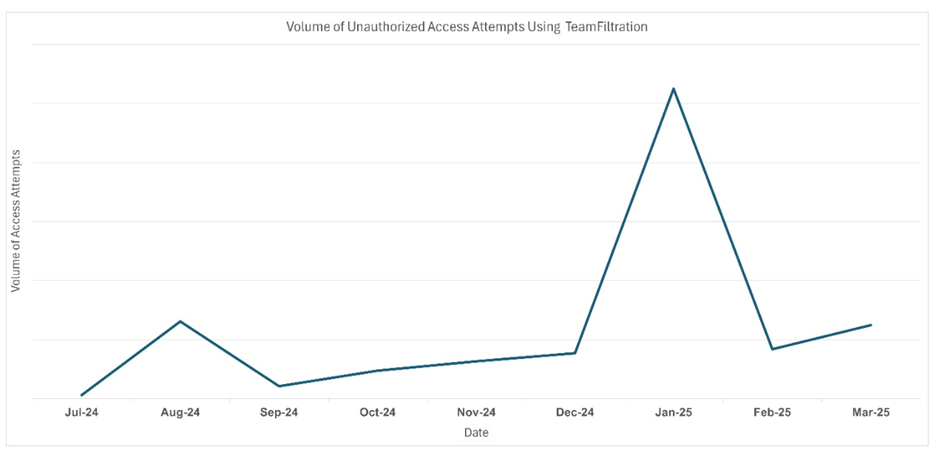
UNK_SneakyStrike velocity by volume of unauthorized access attempts using TeamFiltration over time (July 2024 – March 2025). (Source: Proofpoint)
Notable campaign takeaways:
- The attackers used a low sophistication technique called password spraying, which relies on trying to find common or previously breached passwords across many users accounts rather than brute-forcing a single account to gain initial access. The success of this attack hinged on users reusing weak passwords and organizations not enforcing strong authentication policies.
- The campaign follows a trend where threat actors weaponize legitimate tools and platforms like TeamFiltration and Microsoft Teams API instead of using less effective, traditional intrusion methods. This makes detecting malicious vs. legitimate traffic much more difficult. In this campaign, researchers were able to weed out real-world malicious activity from legitimate penetration tests. They determined UNK_SneakyStrike demonstrated broader, indiscriminate targeting patterns, whereas legitimate red team penetration testing occurred over a smaller window. And since Microsoft Teams is a widely used collaboration tool, its API is often trusted and is less likely to trigger security alerts. This makes Teams an attractive tool for threat actors trying to blend in with legitimate traffic.
- Attackers also relied on AWS infrastructure, which is required by the TeamFiltration tool for intrusion simulations because its password spraying function supports rotation across different AWS regions. Using AWS servers in multiple regions helps attackers bypass geo-based security controls and distribute attacks to avoid detection. As entities have migrated to the cloud, threat actors have followed suit.
Defensive recommendations
Defending against attacks that exploit the Microsoft Teams API and AWS infrastructure for user enumeration and password spraying requires a layered, cloud-aware security strategy. Some key defenses include:
- Conditional access policies: Implement conditional access controls in Microsoft Entra ID. For example, block or challenge logins from unfamiliar geographic locations and require MFA for suspicious sign-ins or new devices.
- Rate limiting and geo-fencing: Apply rate limits to authentication attempts via APIs, restrict access to Teams APIs from known or expected IP ranges, and use geo-fencing to block or alert on traffic from regions where your users don’t operate.
- Monitoring and detection: Enable audit logging and monitor for unusual patterns like repeated failed logins from multiple IDs, or high-volume API calls from cloud providers like AWS. Use SIEM tools to correlate events across services and detect distributed attacks.
- Hardened authentication: Enforce MFA for all users and especially administrators. This adds an extra layer of defense. Even if an attacker got access to a password, MFA is an added blockade to stop them from simply logging in and gaining account access. When you can, use passwordless authentication methods like FIDO2 keys or authenticator apps.
- Use a password manager. A password manager can’t stop attackers from launching password spraying campaigns, but it can help make you a terrible target. The bad guys are going to do what they’re going to do, or at least try, and they’re more likely to go after low-hanging fruit. Password managers like LastPass can help protect against password spraying by promoting strong, unique passwords and generating passwords to avoid weak or recycled passwords, which attackers exploit in spraying. They can also integrate with MFA, adding an extra layer of protection. Additionally, LastPass’ dark web monitoring proactively checks customers' email addresses for breached credentials, so folks could be alerted before malicious activity is attempted.
- User awareness and hygiene: People are the double-edged sword in cybersecurity – they’re often the weakest link but also the first line of defense. Educate users about phishing and credential stuffing so they can be on the lookout for suspicious activity and be informed about why good cyber hygiene, like using unique passwords, matters.



